
This article shows you fool-proof methods on how to secure a Crypto Wallet in very easy steps either you’re a beginner or intermediate Crypto community member.
The issue of insecurity or wallet compromise is so rampant among beginners and intermediate Crypto enthusiasts whereby your crypto wallet can be compromised by someone close to you or get hacked by an experienced hacker on the internet.
So, why is this post important or why should you read every detail to the end?
People lose money all the time regarding this topic and recently, one of the victims whose wallets were compromised lost over ten thousand ($10,000+) worth of $CAKES plus other major coins due to wallet breaches.
Imagine this happened to you, which state would you be in right now and would you take your wallet security seriously?
This and more were the reason why I have taken it upon myself to educate you and other members of the Crypto community on some important, most basics and best practises of security measures you can adopt and practise.
Either you’re a beginner or an intermediate Crypto Trader/Investor, what I’m about to show you will help prevent you from losing your life savings to an intruder or a hacker due to lack of right information.
So, can we begin now? Are you ready for this?
Okay, let’s do it!
How To Easily Become A Vulnerable Target

There are 2 most common ways you could open yourself to threats or an intruder without you even knowing and I will show you now:
- By ignorance or not being careful: by now, you should know that your Smartphone is your business tool and should be treated as one. You have to stop releasing your phone to just anybody all because you don’t want to look like a bad person. And if you can’t do without being strict with your phone, then get another phone for social things and keep the other one strictly for business where only you have access to it.
- By granting full access to your wallet/phone: some peoples’ wallets have been hacked simply because they unknowingly granted access to their wallet either by connecting their wallets to a phishing website or clicking on a phishing link all in the name of doing Airdrops! Airdrops are good and can even make you good money but you should have a seperate wallet for doing Airdrops without your major coins in the same place. That is, avoid putting all your genuine eggs together with Airdrop coins that are not even certain!
Next, I will show you some facts and myths about Crypto wallet addresses before we delve into how to secure a crypto wallet.
Facts And Myths of Crypto Wallet Account
Myth: You can be hacked by giving out your public address.
Fact: You can not be hacked by giving out your public address, you can only be hacked by giving out your private keys and that’s why it’s called private.
Myth: when someone looks up your public address on the Blockchain, it’s easy for the person to see all your coins and hack your account.
Fact: Cryptocurrency and Blockchain are open source projects and anyone can look up your wallet to see all your assets with your public address (also known as your receive address) but they can not tamper or alter your wallet just by having access to your public address.
Myth: Trust Wallet Admins or exchange supports can help you recover your wallet even if you lose your wallet 12 phrases/seeds or private keys.
Fact: Trust Wallet Admins or exchange supports can not help you recover your wallet. Once you expose your 12 phrases to an intruder or a hacker on the internet and your wallet is compromised, there’s nothing anyone can do to it again except for you to open a new wallet.
To the next section..
Incidence Response – What To Do When Your Wallet Is Compromised
These are what to do immediately when you notice that your wallet is compromised or intruded and there’s an unauthorized access and activity going on in your wallet:
- Remain calm and understand how much you would lose in that wallet if you don’t respond to the intrusion immediately.
- Then, open a new wallet immediately and move all your funds there as fast as possible before the intruder or hacker does.
- Try to identify how the intruder came in, did you click on a phishing link, give your phone to an assumed trusted person or you connected your wallet to a website for an Airdrop?
- Calculate how much you’re able to save from losing your funds to the intrusion because of your ability to respond.
- Ensure you take adequate security measures that prevent such an occurrence from happening again in the future.
- One of the wrong things you could do is NOT responding to the incidence and watch the intruder move all your funds away without doing anything. Always practise Incidence Response(IR) at all times.
Next, I am going to present to you 5 best practices to adopt on how to secure a Crypto Wallet either you’re just starting out in Cryptocurrency Trading/Investing or you’ve been in the space for a while but could be vulnerable to threats.
7 Best Practises on How To Secure a Crypto Wallet from Intruders/Hackers

Add an extra-layer security to your Smartphone:
For example, once you set up your wallet, the next thing to do is to add a second level security to your phone.
You could add face unlock, fingerprint, pattern lock or password to secure your phone and prevent unauthorized access into it.
You can go to settings in your TRUST WALLET and enable fingerprint for signing transactions, it helps to ensure only you are able to perform transactions with your fingerprint alone.
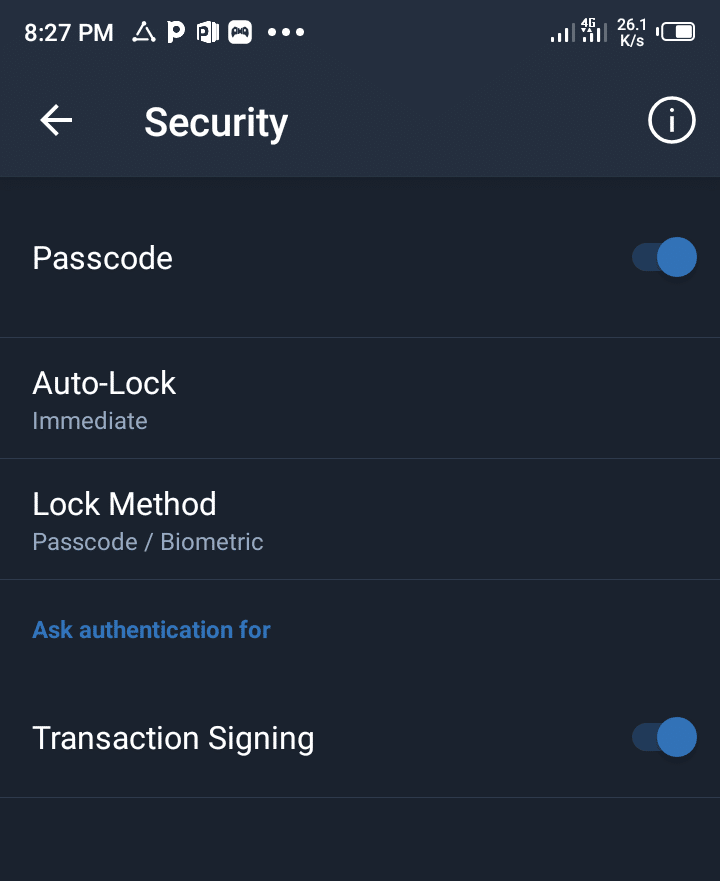
Use 2 Factor Authentication (2FA):
2FA simply refers to second level security that allows you to protect your account apart from your login details(username and password) especially when you’re using an exchange wallet.
Exchanges like BINANCE FTX, BITRUE, LATOKEN, MXC, 5ROI and others ensure you set up your 2FA before you can login or use many of their services to ensure your privacy protection on their platform.
You can download GOOGLE AUTHENTICATOR on Playstore to set it up.
2FA could also mean you using your phone number line or alternative email to receive a permission code each time you’re login into your account or performing a transaction just to ensure that the owner is aware of the transaction going on, on the account to prevent an intruder.
Back Up Your Wallet Seeds or 12 Phrases To Cloud:

if you want to secure your wallet, it’s more advisable to back up your 12 phrases/seeds and private keys in cloud than writing them on paper or saving them on phone.
When you write it on paper, it could get lost easily, if it’s saved inside your phone, there is no way you could recover it if your phone gets lost or it’s wiped and restored to factory settings.
I know some people who have lost their money through this method. The best way I advise, is to back it up into cloud.
And this is easily done since you have a Gmail account, you can use Google Cloud by saving your 12 phrases or private keys in Google Documents (called Docs) online using your single Gmail account and being able to retrieve it easily anytime and anywhere whenever you need it without the fear of losing it.
Though you must have a strong and long gmail password which I will teach you next.
Create a Strong and Long Password for Your Gmail or Exchange Account:
It’s easy to create a Strong and Long password that is easily remembered.
All you need do is create a password between 8 to 15 characters long using either the name of your primary school or best teacher or a village in your locality only you know about.
While you make the first 3 or 4 characters CAPITAL letters, one of the password must be a special character(like +,-,@,#,etc).
Ensure the password also contains numbers (111,007, 127, etc) and write the remaining in small letters.
In practical, here’s an example;
ST@THERESAprim007
This is a standard example of a strong password
This password cannot be easily cracked even if an experienced hacker uses a dictionary attack or brute force attack method because…
It contains all the standard elements recommended to create a strong password and only you know the words inside it.
Undetstanding how to create a strong password is the first step before moving to other strategies on how to secure a crypto wallet.
Install Antivirus To Detect Possible Threats on your phone:
Use Antivirus to scan your smartphone from time to time to detect some apps that could pose threats to your device either to steal your information or to spy on your data.
Search for Antivirus on Playstore and read reviews on it to see the best one to use for your Smartphone.
Use Hardware Wallet To Store Your Assets:
Hardware wallet is another way to secure your coins using hardware wallet.
Hardware wallets are cold wallets that allow you to store your coins on the device offline.
Though they can be expensive, but, you should get one if you can afford it.
It’s another way of backing up your coins elsewhere without the fear of a hacker getting into your offline wallet.
SAFEPAL has a hardware wallet you can get for this purpose. It is very effective and affordable for the maximum security of your Crypto assets and wallet.
KLEVER hardware wallet is still under development, I would update this article once its manufacturing process is completed.
Use a Phone Lock App To Secure Your Smartphone:
I discovered a phone lock app recently and after reading reviews on it on Playstore..
I realised that most of the challenges that were faced by old users of the App have been solved in the improved version and this made me download the App and tried it out and guess what?
The App gave me an amazing experience.
I will talk about the App extensively next. Stay with me…
I made a research into a possible solution on how to secure a Crypto wallet that could solve or at least reduce this level of intrusion experienced by some Crypto community members in my domain.
And below is the result…
Even though, you might have come across this solution and not have been using it, so I thought I should share it with you.
The name of the Application is App Lock which you can download on Google Play Store as an Android user but..
It has 3 features that I enjoyed so much which you must also activate once you download it, I will list and explain them below:
1.) Intruder Selfie: this app lock feature takes the picture of an intruder who’s trying to intrude your privacy using a wrong password/lock pattern and saves it for you to see and recognize the intruder.
You will be able to see this information inside the app as this app tells you the time, date and the particular app the intruder is trying to access without your permission.
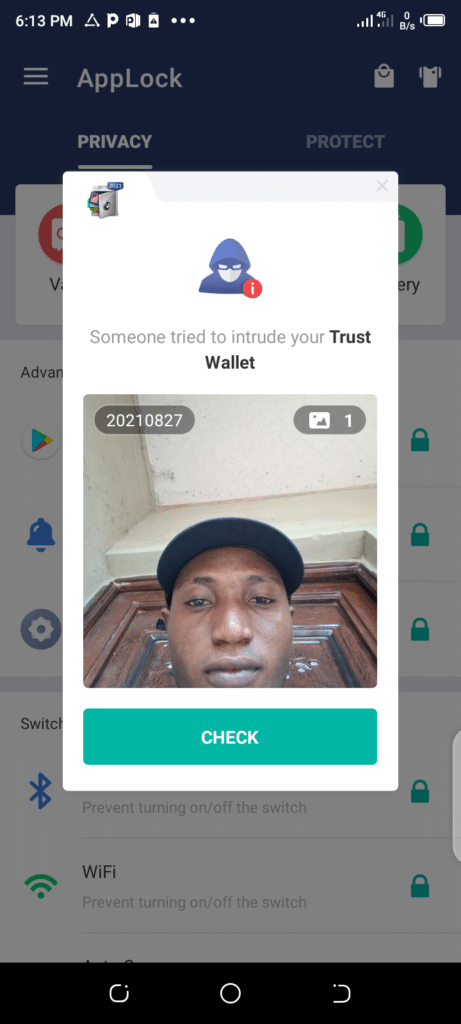
To the next point…
2.) Icon Camouflage: some intruders even know about this App Lock and they might want to find it on your phone and uninstall it, before performing their evil act. But…
You can use this app feature to change the icon logo or activate this third feature I’m about to talk next, as it won’t allow the intruder to uninstall the app on your phone before carrying the intrusion out.
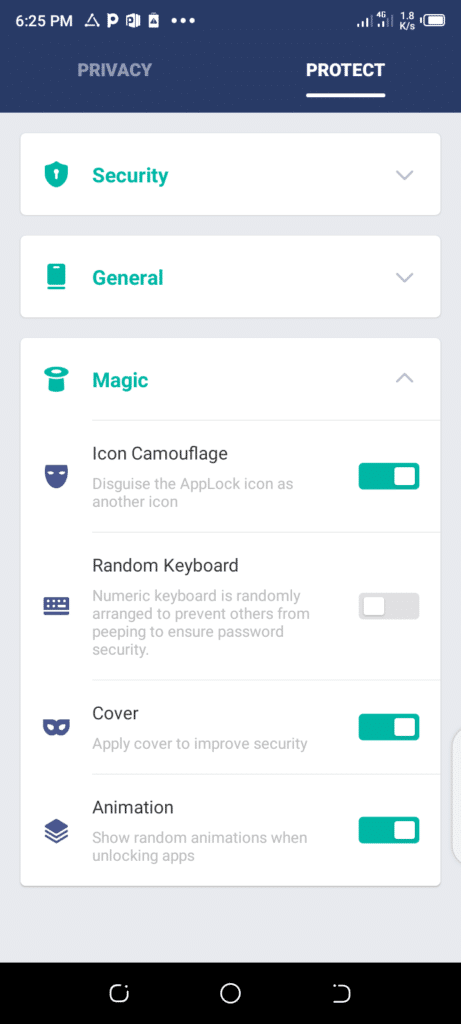
To the next point..
3.) Advanced Protection: With this feature, nobody can uninstall your App lock on your phone because you can connect your email to the app and this gives only you access to uninstall the App from your phone.
You can also set up your security question and answer only you know of as part of its advance security levels.
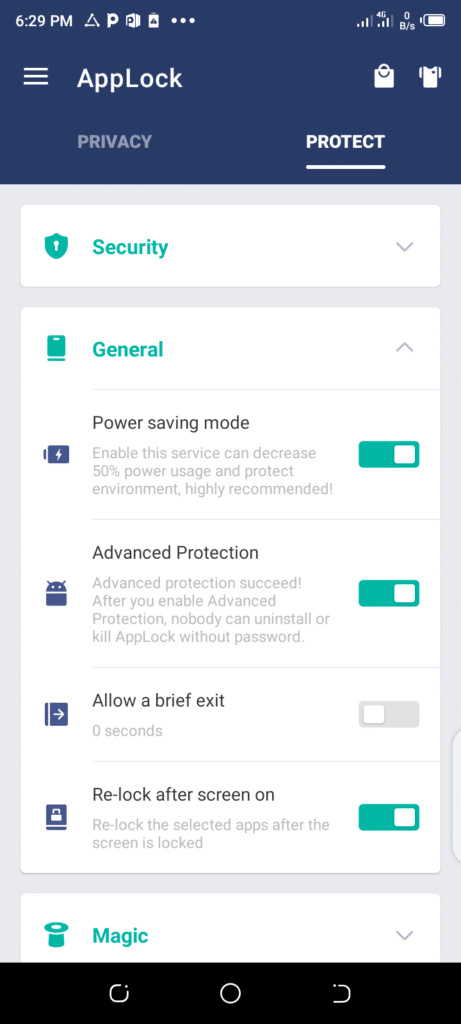
The advantage of this security App is endless when you start using it but…
Though the App is free to use, but, it contains some Ads that pops up when using the App and which is normal since that’s the way the developers also generate their income to improve the App and also solve any security challenges that you experience on the App.
And you can pay for their monthly/yearly service which removes the Ads for you and you can use the App without a single Ads popping at you.
There are many more useful features on this App which you can use to improve your phone security while doing your Crypto business, but…
I’ve decided to discuss the TOP ones I found very useful and important for you.
And there are more free security Apps on Playstore, infact, there could be more better ones but I shared this with you because..
As at the time of writing this post, this App is the only most used Phone lock App on Playstore with over 100K user downloads.
Recommended Article: How To Make Money On Bitcoin Trading – Detailed Beginners Guide
Conclusion: Rounding it off into a Whole Number 1!
I have been able to explain in this article the top 7 best Practises or ways you can use on how to secure your wallet from hackers, how to discover if you’re vulnerable to threats/intrusion and how to practise Incidence Response (IR).
I also showed you the myths and facts about Crypto wallet addresses and many more.
So, I think you can trust this research topic on how to secure a Crypto Wallet if you feel like using the App recommended to protect your privacy as well.
Note: all I know and shared is not for any gain nor am I promoting any service on this App Lock product.
I only shared this App information since security issues have been rampant among the Crypto community, and most beginners especially are the main targets for intruders or hackers.
If you’re new to Crypto Trading and Investing and want to know how you can profit from this space, I recommend you read this article now.
And if you already an existing Trader but have emotions problem when you’re approaching the market, this article I wrote on the history of Jesse Livermore would help you.
If you would like to be part of this community, you can join our Telegram community now.
Before I leave you, let me give you a bonus hint:
There are many scammers online that pretend to be online Admins or supports posing to help you by requesting for your private keys or 12 Phrases, DO NOT GIVE IT TO THEM. Or else, your coins will be wiped off and you will be calmed!
-Mike Akerele
Did you enjoy this article on how to secure a Crypto Wallet? Please, leave a comment and let me know how much it has helped you.
You can also use the comment section to let me know if you have any questions or tell me which of the article points you found really interesting to you.
If there is any other way you protect your wallet that has not been mentioned, please feel free to share it with me and others in the comment section.
Please, use the social share buttons around this post to share this article to Facebook, Twitter and Instagram to reach others who need to see it.
Thanks for taking your time to read to the end.
Stay secured, stay guided!
To your success.
All rights reserved. This material and any other digital content on this website should NOT be reproduced, published, broadcast, written or distributed in full or in part, without written permission from PROFITSTALKING owner.








More wisdom I pray thee@ Profitstalking
Hi Victoria,
Glad you found the article helpful. Thank you for the prayer.
Thanks for the update boss
You’re welcome.
Wao, honestly, this is insightful because one of the greatest fear is about how to secure your wallet and I think this is very great step one must greatly considered. Thank you sir this is helpful and informative.
Hi Moses,
Glad you found the content insightful.
Check other articles around the site for more helpful content written for you.
I really got value from this site. Thanks a bunch.
Hi Hesmy,
Glad you got value from the site and thanks for letting me know.
Appreciate this post. Let me try it out.
Hi, glad you found the content useful.
Go try it out and update me on your trial.
Best of luck.
I’m glad I got value from this! it’s helpful and thank you for the article you shared with us! More knowledge and wisdom
Hi Tobiloba,
It’s nice hearing you got value from this post and I’m glad that it’s helpful for you.
Amen to your prayers and thanks for your detailed feedback.
Try and take action on what you’ve learned.
Itís nearly impossible to find educated people for this topic, but you seem like you know what youíre talking about! Thanks
Thanks to my father who told me concerning this web
site, this blog is really remarkable.